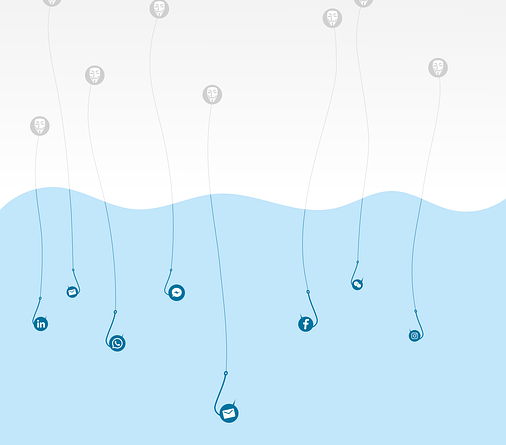
Imagine a world where every device you own is interconnected and constantly communicating with each other. This is the reality of the Internet of Things (IoT), a network of smart devices that has revolutionized the way we live.
From smart homes to wearable devices, the IoT has brought convenience and efficiency to our daily lives. However, with this connectivity comes an increased risk of security breaches. Your smart devices, once vulnerable, can become a gateway for hackers to access your personal information and invade your privacy.
In this article, we will explore the importance of securing your smart devices in the IoT era. We will discuss the common security risks that come with IoT devices and provide practical tips on how to safeguard your network and protect your data.
By understanding the potential threats and taking proactive measures, you can ensure a safer and more secure IoT experience.

Introduction
Are you ready to dive into the world of IoT security and discover why it’s crucial to protect your smart devices?
In today’s interconnected world, IoT security plays a vital role in safeguarding our smart devices. With the increasing number of devices connected to the internet, the need for robust security measures has become more important than ever.
One of the key aspects of IoT security is device authentication, which ensures that only authorized devices can access the network.
Additionally, regular firmware updates are essential to address any vulnerabilities and enhance the device’s security features.

Another crucial element is encryption, which protects the data transmitted between devices and prevents unauthorized access.
By implementing these security measures, we can ensure the safety and privacy of our smart devices in an increasingly connected world.
Understanding the Internet of Things (IoT)
In this discussion, you’ll explore the definition and examples of IoT devices. IoT devices refer to physical objects that are connected to the internet and can collect and exchange data. Examples include smart thermostats, wearable fitness trackers, and voice-controlled assistants.
By adopting IoT technology, you can enjoy benefits such as increased convenience, efficiency, and connectivity. However, it’s important to be aware of the potential risks that come with the adoption of IoT devices. These risks include security vulnerabilities and privacy concerns.

Definition and Examples of IoT Devices
One of the most fascinating aspects of the Internet of Things (IoT) is the vast array of smart devices that are revolutionizing our daily lives. These IoT devices are connected to the internet and can communicate with each other, providing us with unprecedented convenience and efficiency.
Examples of IoT devices include smart home appliances, such as thermostats and security cameras, which can be controlled remotely through smartphone apps. Wearable fitness trackers, such as smartwatches and fitness bands, also fall under the category of IoT devices. These devices can monitor and track various health metrics, such as heart rate and sleep patterns, and sync the data to a smartphone or computer for analysis.
However, with the rise of these interconnected devices comes the pressing need for IoT security. IoT security issues and challenges have become a major concern, as these devices can be vulnerable to hacking and unauthorized access. Ensuring the security of your IoT devices is crucial to protect your personal information and maintain the privacy of your home.
Taking steps to enhance IoT device security is essential in this increasingly connected world. This can include regularly updating firmware to ensure the latest security patches are in place. It is also important to use strong, unique passwords for each IoT device and enable two-factor authentication whenever possible. Additionally, being mindful of the data collected by IoT devices and carefully reviewing privacy settings can help protect your personal information.

In conclusion, the definition and examples of IoT devices illustrate the convenience and efficiency they bring to our lives. However, it is important to prioritize IoT security to safeguard our personal information and maintain privacy in an interconnected world.
Benefits and Risks of IoT Adoption
Maximize the manifold merits and minimize the potential perils of embracing the Internet of Things by cautiously considering the compatibility, convenience, and connectivity of adopting interconnected devices.
The benefits of IoT adoption are plentiful, with enhanced convenience and connectivity being at the forefront. Smart devices allow for seamless integration and automation, making daily tasks easier and more efficient.
However, it’s important to acknowledge the risks that come with this level of connectivity. IoT security is a major concern, as interconnected devices can potentially be exploited by cybercriminals. Increased cybersecurity vulnerabilities can lead to privacy breaches, data theft, and even physical harm.

To secure your smart devices, it is crucial to prioritize security measures such as strong passwords, regular software updates, and network segmentation.
By balancing the benefits and risks of IoT adoption and implementing adequate security measures, you can fully enjoy the advantages of a connected lifestyle while minimizing potential vulnerabilities.
Common IoT Security Risks
When it comes to IoT security risks, there are several key points to consider.
First, inadequate device authentication can leave your smart devices vulnerable to unauthorized access.

Second, weak or default passwords are a common security issue that can be easily exploited by hackers.
Lastly, vulnerabilities in firmware and software can provide an entry point for attackers to compromise your IoT devices.
It is important to be aware of these risks and take necessary steps to secure your smart devices.
Inadequate Device Authentication
Ensure your smart devices are properly authenticated to prevent unauthorized access and protect your personal information. Inadequate device authentication is one of the major IoT security risks that can leave your smart devices vulnerable to attacks. With the increasing number of internet of things vulnerabilities, it is crucial to take necessary steps to secure your smart devices.

Device authentication is the process of verifying the identity of a device before granting access to it. Without proper authentication, cybercriminals can easily gain unauthorized access to your smart devices and exploit them for malicious purposes. This can lead to the compromise of your personal data, invasion of privacy, and even control over your devices.
To enhance device authentication and strengthen IoT security, make sure to use strong and unique passwords for each of your smart devices. Additionally, consider implementing two-factor authentication, which adds an extra layer of security by requiring a second form of verification, such as a fingerprint or a unique code sent to your mobile device.
By prioritizing device authentication, you can significantly reduce the risk of unauthorized access and protect your smart devices from potential attacks. Remember, securing smart devices is essential to safeguarding your personal information in the age of the internet of things.
Weak or Default Passwords
One way to address the risk of weak or default passwords is by using strong and unique passwords for each of your connected devices.

When it comes to IoT security, it is crucial to ensure that your smart devices have strong passwords to protect them from potential cyber attacks. Weak passwords make it easier for hackers to gain unauthorized access to your devices and compromise your personal information.
Using default passwords is especially risky since they are often widely known and easily guessed by attackers. To secure your devices, create passwords that are long, complex, and include a combination of uppercase and lowercase letters, numbers, and special characters.
Additionally, avoid using the same password for multiple devices to prevent hackers from accessing all your connected devices if one password is compromised.
By following these practices, you can significantly enhance the security of your IoT devices.

Vulnerabilities in Firmware and Software
Protecting your connected devices involves addressing vulnerabilities in the firmware and software they run on. Firmware refers to the embedded software that controls the functionality of your smart devices, while software encompasses the applications and programs that run on them.
Both firmware and software can contain vulnerabilities that hackers can exploit to gain unauthorized access or control over your devices. These vulnerabilities can range from weak encryption protocols to outdated software versions that lack necessary security patches.
To mitigate these risks, it is crucial to regularly update your firmware and software to the latest versions provided by the manufacturers. Additionally, implementing strong encryption and authentication mechanisms can add an extra layer of protection to prevent unauthorized access to your smart devices.
By actively addressing vulnerabilities in firmware and software, you can enhance the security of your internet of things (IoT) devices.

Lack of Encryption and Data Protection
Lack of encryption and data protection puts connected devices at risk. A staggering 93% of cyber attacks target vulnerabilities in firmware and software. In the world of IoT security, data protection is crucial to safeguarding your smart devices.
Without encryption, hackers can easily intercept and manipulate your sensitive information, potentially causing irreparable damage. To mitigate this risk, it is essential to choose devices from reputable manufacturers who prioritize security. Reputable manufacturers invest in robust encryption methods, ensuring that your data remains secure and protected.
Additionally, regular firmware and software updates are vital to address any potential vulnerabilities. By staying vigilant and proactive in securing your IoT devices, you can minimize the risk of falling victim to cyber attacks and protect your valuable data.
Insecure Wireless Communication
To ensure the safety of your connected devices, it is crucial to address the issue of insecure wireless communication. In today’s world, where everything is connected, wifi security plays a vital role in protecting your smart devices from potential threats.

The internet of things (IoT) security landscape is constantly evolving, and the risks associated with insecure wireless communication are increasing. Hackers can exploit vulnerabilities in your IoT devices, intercept sensitive data, and gain unauthorized access to your network.
One of the major IoT security threats is the lack of proper encryption and data protection during wireless communication. Without proper encryption, hackers can easily eavesdrop on your data transmissions and manipulate the information being sent or received. Moreover, insecure wireless communication can lead to unauthorized access to your IoT devices, enabling attackers to control, manipulate, or even disable them.
To mitigate these risks, it is essential to implement strong wifi security measures. This includes using strong passwords, regularly updating firmware, and ensuring that your IoT devices are connected to secure and encrypted networks.
Additionally, implementing robust IoT device authentication protocols can help in preventing unauthorized access to your smart devices. By prioritizing wifi security and taking necessary precautions, you can ensure the safety of your connected devices and protect your privacy.

Securing Your Smart Devices
When it comes to securing your smart devices, there are several key points to consider.
First, make sure to use strong passwords and authentication methods to prevent unauthorized access.
Additionally, regularly update the firmware and software of your devices to stay protected against known vulnerabilities.
Lastly, consider implementing network segmentation and firewall protection, as well as enabling encryption and data protection features, to further enhance the security of your smart devices.

Strong Passwords and Authentication
To ensure the security of your smart devices, it is crucial to take proactive measures. Implementing strong passwords and authentication methods can mitigate potential threats. Weak or default passwords make it easier for hackers to gain access to your devices and compromise your privacy. By using unique, complex passwords that include a combination of letters, numbers, and special characters, you can significantly enhance your device’s security.
Additionally, enabling two-factor authentication adds an extra layer of protection. This requires a second form of verification to access your devices. By doing so, you reduce the risk of falling victim to internet of things attacks and ensure your peace of mind.
Regular Firmware and Software Updates
Now that you understand the importance of strong passwords and authentication for securing your smart devices, it’s time to delve into another crucial aspect of IoT security: regular firmware and software updates.
Keeping your devices up to date with the latest patches and security fixes is essential in protecting them from vulnerabilities and potential cyberattacks. Firmware updates ensure that the embedded software in your devices is running smoothly and securely, while software updates provide necessary bug fixes and performance enhancements.

By regularly updating your smart devices, you can stay one step ahead of hackers and ensure the ongoing security of your IoT ecosystem. Don’t underestimate the power of these updates – they are your first line of defense in the ever-evolving world of internet of things security.
Network Segmentation and Firewall Protection
By isolating IoT devices from the main network and implementing network segmentation and firewall protection, you can create a secure barrier that shields your connected devices from potential cyber threats.
Network segmentation involves dividing your network into smaller, isolated segments to limit the spread of an attack and protect sensitive data. This strategy ensures that if one IoT device is compromised, the rest of your network remains unaffected.
Additionally, implementing a firewall adds an extra layer of defense by monitoring and controlling incoming and outgoing traffic to prevent unauthorized access. This approach is crucial for internet of things (IoT) security and privacy, as it addresses key IoT security issues and solutions.

By adopting a comprehensive IoT security architecture that includes network segmentation and firewall protection, you can minimize the risk of cyber attacks and safeguard your smart devices.
Encryption and Data Protection
Take the time to fortify your files and shield your sensitive information through the power of encryption and data protection.
When it comes to IoT security and securing your smart devices, encryption and data protection are crucial.
Encryption involves converting your data into a code that can only be accessed with the correct decryption key, making it unreadable to unauthorized individuals. This ensures that even if your data is intercepted, it remains secure.
Data protection goes beyond encryption by implementing measures to prevent unauthorized access or alteration of your data. This can include implementing strong access controls, regularly updating software and firmware, and using secure communication protocols.
By prioritizing encryption and data protection, you can enhance the security of your smart devices and safeguard your sensitive information in the ever-expanding world of IoT security.
Configuring Device Privacy Settings
To ensure the privacy of your connected devices, it is crucial to address IoT security concerns. Configure device privacy settings according to your preferences to enhance IoT privacy and security. Take advantage of available options such as password protection, encryption, and two-factor authentication. Stay updated with the latest IoT security protocols and firmware updates. Regularly review and adjust your device privacy settings to ensure the security of your personal information and protection from potential threats.
Disabling Unnecessary Features and Services
Disabling unnecessary features and services on your connected devices is like decluttering your home, removing unnecessary items to create a clean and organized living space. When it comes to IoT security, it is crucial to disable any features or services that you do not use regularly.

By doing so, you minimize the attack surface and reduce the risk of potential vulnerabilities. Hackers often target IoT devices through these unnecessary features and services, exploiting weaknesses to gain unauthorized access.
For example, some IoT attacks have exploited default settings or unused features to compromise smart devices. Therefore, it is essential to thoroughly review and disable any features or services that you don’t need.
This simple step can significantly enhance your internet of things cybersecurity and protect your smart devices from potential attacks.
IoT Network Security
When it comes to IoT network security, there are two key points you should focus on:

- Securing your Wi-Fi networks:
- Use strong passwords.
- Enable network encryption.
- Change default router settings.
Implementing network security solutions:
- Use firewalls.
- Set up a virtual private network (VPN).
- Regularly update firmware and software.
By taking these steps, you can ensure that your IoT devices are protected from potential threats and maintain a secure network environment.
Securing Wi-Fi Networks
Securing your Wi-Fi network is essential for protecting your smart devices. It ensures that unauthorized users cannot gain access to your personal information. With the increasing number of smart devices connected to the internet, IoT security has become a critical concern. One of the main risks of the internet of things is the potential for hackers to exploit vulnerabilities in Wi-Fi networks.
To mitigate these risks, it is crucial to implement strong passwords and encryption for your Wi-Fi network. Make sure to use a unique and complex password that includes a combination of letters, numbers, and special characters. Additionally, enabling encryption protocols such as WPA2 or WPA3 provides an extra layer of security.

Regularly updating your Wi-Fi router’s firmware and using network security solutions like firewalls can further enhance the security of your smart devices.
By taking these steps, you can significantly reduce the chances of unauthorized access to your smart devices and protect your personal information.
Implementing Network Security Solutions
Now that you have secured your Wi-Fi network, it’s time to take a step further in protecting your smart devices.
With the rapid growth of the Internet of Things (IoT), it’s crucial to prioritize IoT security. Securing your smart devices is essential to prevent potential vulnerabilities and protect your personal information.

This is where implementing network security solutions comes into play. By doing so, you can safeguard your IoT devices from various internet of things security risks.
Network security solutions such as firewalls and intrusion detection systems (IDS) can help detect and block any unauthorized access to your smart devices.
Additionally, regularly updating firmware and using strong and unique passwords for each device are important steps to enhance security.
By taking these precautions, you can ensure a safer and more secure online experience for your smart devices.

Safeguarding IoT Devices at Home
When it comes to safeguarding your IoT devices at home, there are a few key points to consider.
First, take physical security measures to protect your devices from theft or tampering. This can include keeping them in secure locations or using locks and alarms.
Second, make sure to thoroughly review and verify the manufacturers of your IoT devices to ensure they have a good track record for security.
Lastly, actively monitor the behavior and activity of your devices to detect any suspicious or unauthorized actions.

Physical Security Measures
When it comes to physical security measures for IoT devices, there are several steps you can take to protect your devices from theft or unauthorized access.
- Adhere to IoT security standards, which are guidelines set by regulatory bodies to ensure the safety and security of IoT devices.
- Seek out IoT security companies that specialize in providing security solutions for smart devices. They offer services such as IoT security testing to identify vulnerabilities and strengthen the overall security of your devices.
Implementing physical security measures like installing locks or alarms can also deter potential thieves. Examples of physical security measures include:
- Using strong passwords
- Encrypting data
- Keeping firmware up to date
By taking these precautions, you can ensure the protection of your IoT devices and the valuable data they hold.
Reviewing and Verifying IoT Device Manufacturers
To ensure your technology remains impervious to threats, it’s essential to carefully vet and endorse reputable brands and vendors for your connected devices.

When it comes to securing the Internet of Things (IoT), reviewing and verifying IoT device manufacturers becomes crucial. With the growing IoT security market, it’s imperative to choose manufacturers that prioritize security measures. Look for companies that have a track record of implementing robust security protocols and regularly release firmware updates to address vulnerabilities.
Additionally, consider manufacturers that actively participate in IoT security projects and collaborate with industry experts. By selecting trusted brands, you can minimize the risk of IoT security problems and ensure that your devices are equipped with the necessary IoT security tools to safeguard against potential threats.
Monitoring Device Behavior and Activity
Now that you’ve reviewed and verified the manufacturers of your IoT devices, it’s crucial to focus on monitoring device behavior and activity to ensure their security.
With the rise of industrial IoT and healthcare IoT, robust IoT security is paramount. By closely monitoring device behavior and activity, you can detect any anomalies or suspicious patterns that may indicate potential IoT security attacks.

This proactive approach allows you to take immediate action and prevent unauthorized access or data breaches. Regularly monitoring your IoT devices helps ensure IoT data security, safeguarding sensitive information and protecting user privacy.
Stay vigilant and regularly monitor your IoT devices to maintain a secure and reliable network.
Privacy and Data Protection
When it comes to privacy and data protection in the context of IoT devices, there are three key points you should understand.
First, it’s important to know how your data is being collected and used by these devices.

Second, make sure to carefully review the privacy policies and terms of service for each device you own.
Lastly, take steps to minimize data sharing and exposure to protect your personal information.
Understanding Data Collection and Usage
Understanding data collection and usage is essential in the world of IoT cyber security. The rapid growth of IoT devices has led to an explosion of data being generated and shared. These devices continuously collect valuable information, such as your smart thermostat learning your daily routine or your fitness tracker monitoring your health.
However, the increasing number of devices connected to the internet has also increased the risks of IoT and security vulnerabilities. It is crucial to understand how your data is being collected, stored, and used by these devices. Implementing an IoT security platform can help protect your sensitive information and ensure that your data is used responsibly and securely.

Reviewing Privacy Policies and Terms of Service
Take a moment to pause and reflect on the potential implications of blindly accepting privacy policies and terms of service before connecting your life to these digital wonders. When it comes to IoT security, reviewing privacy policies and terms of service is crucial.
These documents outline how your personal data will be collected, used, and protected by the IoT devices you bring into your home. By carefully reviewing these policies, you can ensure that your information is being handled responsibly and that your privacy is being respected.
Look for clear and transparent explanations of data collection practices, as well as information on how the company handles security breaches. Make sure the IoT security products you choose have a comprehensive IoT security policy in place, so you can have peace of mind knowing that your smart devices are protecting your data.
Minimizing Data Sharing and Exposure
To ensure the safety of your personal information, it is essential to limit the extent of data sharing and exposure when connecting your life to the digital world. Internet of Things (IoT) security is a critical aspect of protecting your smart devices from cyber threats.

Minimizing data sharing and exposure helps reduce the risk of unauthorized access and potential misuse of your sensitive information. By carefully reviewing the privacy settings of each device and application, you can control what data is shared and with whom.
Additionally, regularly updating your devices’ firmware and software can address any known vulnerabilities and strengthen the overall security of your IoT ecosystem. This is especially important in sectors like healthcare, where IoT vulnerabilities can have severe consequences for patient privacy and safety.
Stay vigilant and take proactive steps to safeguard your data in the ever-expanding world of IoT.
Educating Users on IoT Security
To ensure the security of your smart devices, it’s important to raise awareness of the risks and best practices associated with the Internet of Things (IoT).

By educating users about potential threats and vulnerabilities, you can empower them to make informed decisions and take necessary precautions.
Providing user guides and resources can further assist users in understanding how to properly secure their devices.
Encouraging responsible IoT usage promotes a safer and more secure connected environment for everyone.
Raising Awareness of IoT Risks and Best Practices
Raising awareness of IoT risks and best practices is crucial in ensuring the security of your internet of things (IoT) devices.

With the increasing number of connected devices, it is essential to understand the potential threats they pose and the steps you can take to mitigate those risks.
By educating yourself and others about the importance of IoT security, you can make informed decisions when choosing and using IoT devices.
Implementing an effective IoT security system and staying updated on internet of things security solutions will help protect your personal information and prevent unauthorized access to your devices.
Additionally, understanding the challenges in IoT security, such as medical IoT security, will enable you to take necessary precautions and ensure the safety of your smart devices.

Providing User Guides and Resources
Now that you are aware of the risks and best practices associated with IoT, it is important to equip yourself with the necessary knowledge and resources to secure your smart devices.
Providing user guides and resources is a crucial step in ensuring the security of your Internet of Things (IoT) devices. These guides can help you understand the different security features and settings available on your devices, and how to properly configure them to protect against potential threats.
Additionally, these resources can provide you with information on the latest IoT security trends, best practices, and examples of IoT security breaches. By familiarizing yourself with these materials, you can stay informed and make informed decisions when it comes to safeguarding your IoT devices and data.
Encouraging Responsible IoT Usage
Ensuring responsible usage of connected devices requires a thorough understanding of the potential risks and a commitment to implementing necessary precautions.

With the rapid growth of the Internet of Things (IoT), it is crucial to prioritize cybersecurity and address the vulnerabilities that come with this interconnected world.
Educating users about the importance of responsible IoT usage is essential to safeguarding personal data and privacy. By providing clear guidelines and resources on best practices, users can learn how to secure their smart devices and minimize the risk of cyberattacks.
Encouraging responsible IoT usage also involves promoting regular software updates, strong passwords, and avoiding default settings.
By fostering a culture of responsible usage, we can collectively enhance the security of the IoT ecosystem and protect ourselves from potential threats.

Future of IoT Security
In the future of IoT security, industry initiatives and standards will play a crucial role in ensuring the safety of your smart devices. These initiatives aim to establish guidelines and best practices for manufacturers, service providers, and consumers to follow.
Additionally, there will be continual advancements and innovations in IoT security solutions to keep up with the ever-evolving threats and vulnerabilities.
Stay informed and proactive in adopting these measures to protect your IoT devices.
Industry Initiatives and Standards
Let’s dive into the fascinating world of industry initiatives and standards for IoT security. A variety of frameworks and certifications are shaping the way we secure our smart devices.

One prominent initiative is the NIST IoT security framework, developed by the National Institute of Standards and Technology. This framework provides guidelines and best practices for securing IoT devices and networks.
Additionally, industry initiatives are focusing on leveraging blockchain technology for IoT security. Blockchain can enhance device authentication, data integrity, and secure communication in IoT ecosystems.
As the IoT industry continues to grow, so do the vulnerabilities and risks associated with it. Industry initiatives and standards play a crucial role in addressing these challenges and ensuring the security of IoT devices.
It is important to stay vigilant and proactive in protecting against attacks on IoT devices, as they can have significant consequences for individuals and industries alike.

Innovations in IoT Security Solutions
Amidst the ever-evolving landscape of connected technology, a new wave of cutting-edge solutions is emerging to safeguard our digital lives and fortify our interconnected world.
With the rise in IoT device attacks, the need for robust internet of things and cyber security has become paramount. Innovations in IoT security solutions are addressing this challenge head-on.
One such innovation is the use of encryption to protect the data transmitted between IoT devices and the cloud. This ensures that only authorized parties can access and interpret the information, reducing the risk of data breaches.
Additionally, advancements in securing WiFi networks have made it harder for hackers to infiltrate IoT devices through weak or unprotected connections.

These innovations are paving the way for a safer and more secure IoT ecosystem.
Conclusion
To wrap things up, you’re now equipped with the knowledge to fortify your smart devices and ensure a safer connected environment in the world of IoT security.
It is crucial to understand that hacking IoT devices is a significant concern. These devices are vulnerable to various attacks due to their interconnected nature.
One essential measure to enhance security is keeping the firmware of your devices up to date. Manufacturers often release firmware updates to address security vulnerabilities and enhance device performance.
Additionally, encryption plays a vital role in protecting your IoT devices. By encrypting the data transmitted between devices and ensuring secure communication channels, you can prevent unauthorized access and safeguard your sensitive information.
Remember, investing in IoT security measures is essential to create a secure and protected environment for your smart devices.
So, there you have it – the ins and outs of IoT security. Now, armed with this knowledge, you can confidently navigate the vast world of smart devices.
Remember, staying vigilant is the key to keeping your data safe from prying eyes. With a little effort, you can ensure that your IoT network remains impenetrable.

Don’t let the ever-evolving landscape of technology intimidate you; embrace it, and let your smart devices serve you without worry.
Happy and secure IoT-ing!
You might also like to read on these cybersecurity articles on Get Hitch
Secure File Sharing: Best Practices for Protecting Sensitive Data
Cybersecurity for Remote Workers: Ensuring Data Security from Anywhere